BGP RTBH - Remotely triggered blackholing is used for DDOS prevention for a long time by many companies. DDOS - Distributed Denial of Service Attacks have an economic impact. According to an NBC News article, More than 40% of DDOS Attacks cost $1 million per day.
Remote Triggered Blackhole is a technique that is used to mitigate DDOS attacks dynamically.
Before RTBH, customers used to call the Operator when there is an attack, Operator NOC engineers used to connect to the attacked network, trace the source of the attack, place the filters accordingly and the attack goes away.
Manual operation is open to configuration mistakes, cannot scale in large networks, and between the attack and the required action, services stay down
There are two types of RTBH
Destination based RTBH
Source-based RTBH
Let's have a look at both of them in this blog post.
Destination-Based BGP RTBH - Remotely Triggered Blackholing
The first RTBH idea was Destination-based RTBH.With this technique, SP and the Customer agree on the discard community.
When there is an attack on the server, the victim (customer) sends the server prefix with the previously agreed community value.
When SP receives the update with that community, action is set to next-hop to null, so the packet is dropped before reaching the customer link
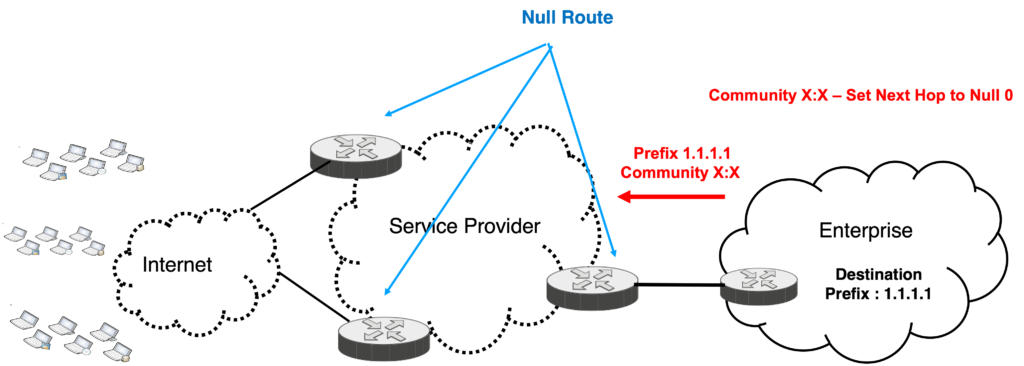
Picture - Destination-based RTBH - Remotely Triggered Blackholing
The problem with this attack is the server will not be reachable from legitimate sources too. The attack is completed but at least the other services might stay up
Also, a customer might change the IP address of the attacked server in DNS, which might take time to propagate this though.
RFC 3882 covers Destination based RTBH
Better than manual processing. Requires pre-configuration of the null route on all edge routers in the SP network
Source-based BGP RTBH - Remotely Triggered Blackholing
RFC 5635 brings the idea of Source RTBH. Instead of the customer specifying the attacked system IP address to the SP, the customer calls SP that they are under attack
By combining uRPF and discard route (null route) configuration, based on the attack source, DDOS is mitigated (In theory)


