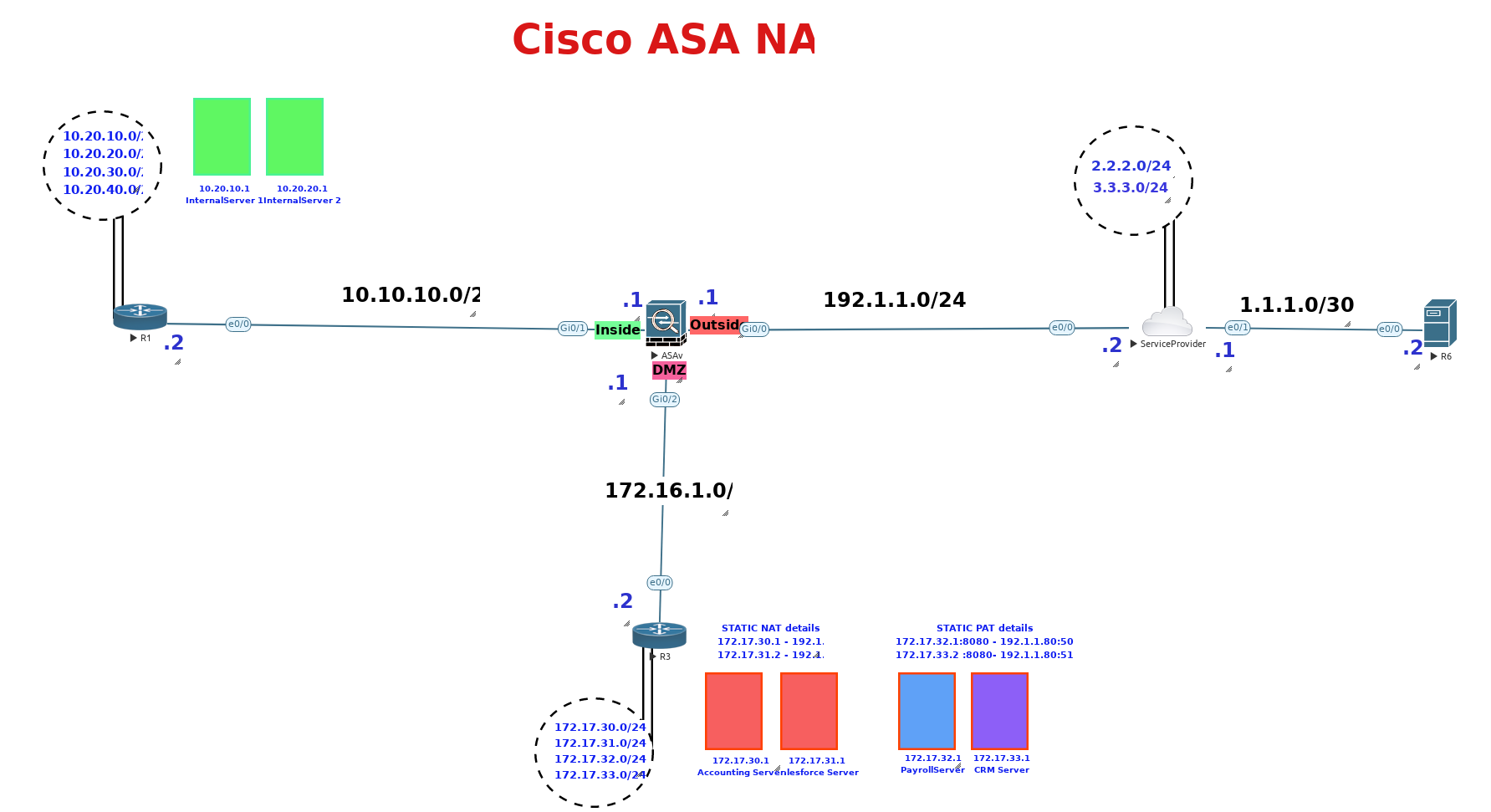
Master the art of ASA NAT in this hands-on lab, where you'll dive deep into every NAT type—Static, Dynamic, Twice NAT, Policy NAT, and more—to ensure seamless and secure traffic flow in real-world networks!
- Category: CCIE Security
Enhance Your IT Skills with OrhanErgun.net Online Training in Networking, Security, and Cloud Technologies.

Master the art of ASA NAT in this hands-on lab, where you'll dive deep into every NAT type—Static, Dynamic, Twice NAT, Policy NAT, and more—to ensure seamless and secure traffic flow in real-world networks!
Our IT rack rental service allows you to access any lab on our website using credits. Here's how it works:
Enjoy flexible and easy access to all our IT labs with our convenient credit system!
Network Address Translation (NAT) on Cisco Adaptive Security Appliance (ASA) is a crucial feature that controls how IP addresses are translated between private and public networks, ensuring security, scalability, and efficient traffic management. ASA supports various NAT types, including Dynamic NAT, which assigns public addresses from a pool, and Static NAT, which provides one-to-one mapping for hosting services.
Policy NAT and Twice NAT allow for advanced translations based on source, destination, and even port numbers, offering granular control over traffic flow.
Mastering these NAT techniques is essential for CCIE Security candidates, as they play a vital role in firewall security, VPNs, and enterprise connectivity.
You might also be interested in these labs:
The default username and password for images used in this course is as follows, however you will hear new passwords during the course if the instructor changes the credentials:
Image name | Username | Password |
IOL images | No username | No password |
CSR1000v | Admin | Admin |
C8000v | Admin | admin |
Viptela devices | Admin | admin |
Windows Server | Administrator | Test123 |
IOS-XR | Admin | Enter new password |
Cisco ASA 802 | no username | no passwd, hit enter |
Cisco ASA 8.4.2, 9.1.5 | no username | no passwd, hit enter |
Cisco ASAv | no username | no passwd, hit enter |
Cisco IPS | cisco | ciscoips123 |
Cisco WSA | admin | ironport |
Cisco ESA | admin | ironport |
Cisco WAAS | admin | default |
Cisco XR9K | Cisco | Cisco |
Cisco NX9K | admin | admin |