Master the art of multi-context firewalls! Dive into CCIE Security - ASA Lab 8 and learn how to configure Cisco ASA contexts using subinterfaces for ultimate network segmentation and security.
- Category: CCIE Security
Enhance Your IT Skills with OrhanErgun.net Online Training in Networking, Security, and Cloud Technologies.

Master the art of multi-context firewalls! Dive into CCIE Security - ASA Lab 8 and learn how to configure Cisco ASA contexts using subinterfaces for ultimate network segmentation and security.
Our IT rack rental service allows you to access any lab on our website using credits. Here's how it works:
Enjoy flexible and easy access to all our IT labs with our convenient credit system!
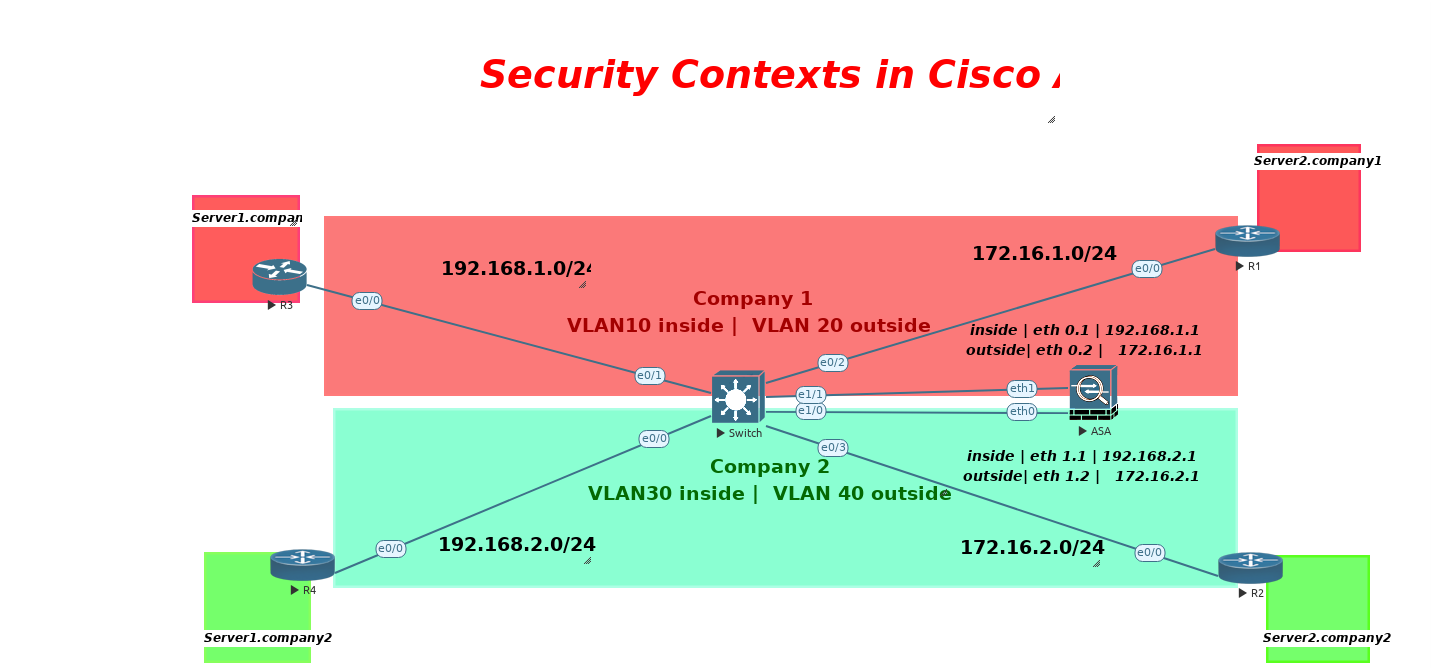
Cisco ASA Multi-Context Mode allows a single firewall to be virtualized into multiple independent security contexts, each functioning as a separate firewall instance with its own policies, interfaces, and administrative control. When using subinterfaces, VLAN tagging (802.1Q) enables efficient traffic segmentation within a shared physical interface, optimizing resource utilization without requiring additional hardware. This approach is widely used in multi-tenant environments, managed security services, and data centers, where multiple customers or departments need isolated security policies.
By implementing ASA contexts with subinterfaces, organizations achieve scalability, flexibility, and enhanced security, ensuring strict separation of traffic flows while maintaining centralized management.
You might also be interested in these labs:
The default username and password for images used in this course is as follows, however you will hear new passwords during the course if the instructor changes the credentials:
Image name | Username | Password |
IOL images | No username | No password |
CSR1000v | Admin | Admin |
C8000v | Admin | admin |
Viptela devices | Admin | admin |
Windows Server | Administrator | Test123 |
IOS-XR | Admin | Enter new password |
Cisco ASA 802 | no username | no passwd, hit enter |
Cisco ASA 8.4.2, 9.1.5 | no username | no passwd, hit enter |
Cisco ASAv | no username | no passwd, hit enter |
Cisco IPS | cisco | ciscoips123 |
Cisco WSA | admin | ironport |
Cisco ESA | admin | ironport |
Cisco WAAS | admin | default |
Cisco XR9K | Cisco | Cisco |
Cisco NX9K | admin | admin |