Unleash the full power of Cisco ASA Multi-Context Mode! In CCIE Security - ASA Lab 7, master the deployment of security contexts using dedicated physical interfaces for ultimate isolation and control
- Category: CCIE Security
Enhance Your IT Skills with OrhanErgun.net Online Training in Networking, Security, and Cloud Technologies.

Unleash the full power of Cisco ASA Multi-Context Mode! In CCIE Security - ASA Lab 7, master the deployment of security contexts using dedicated physical interfaces for ultimate isolation and control
Our IT rack rental service allows you to access any lab on our website using credits. Here's how it works:
Enjoy flexible and easy access to all our IT labs with our convenient credit system!
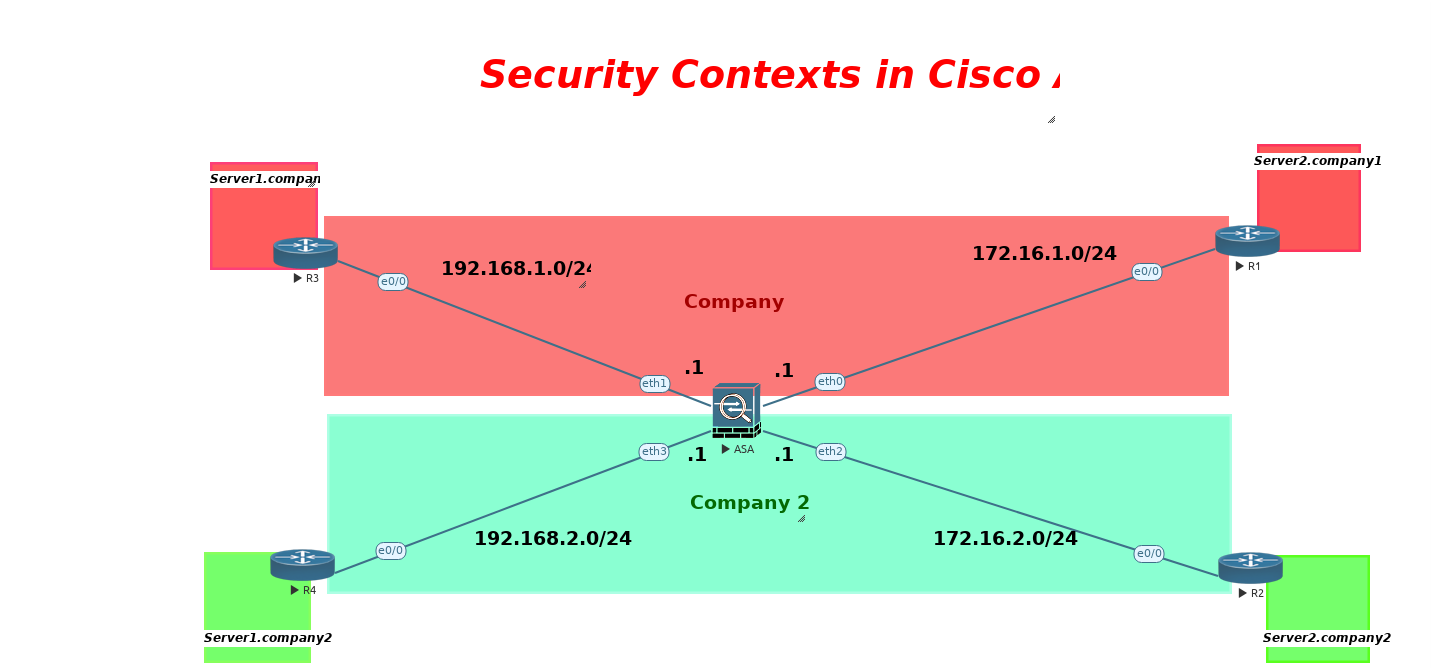
Cisco ASA Multi-Context Mode enables the creation of multiple virtual firewalls within a single ASA device, each operating independently with its own security policies, configurations, and administrative access. By using dedicated physical interfaces for each context, organizations achieve complete traffic isolation, ensuring that no cross-context interference occurs.
This approach is ideal for high-security environments, service providers, and enterprises that require strict separation of network segments or tenants. Unlike subinterfaces, which rely on VLAN tagging, physical interfaces provide enhanced performance, security, and compliance by eliminating shared bandwidth concerns.
Deploying ASA contexts with physical interfaces ensures maximum security and control, making it a preferred solution for mission-critical networks.
You might also be interested in these labs:
The default username and password for images used in this course is as follows, however you will hear new passwords during the course if the instructor changes the credentials:
Image name | Username | Password |
IOL images | No username | No password |
CSR1000v | Admin | Admin |
C8000v | Admin | admin |
Viptela devices | Admin | admin |
Windows Server | Administrator | Test123 |
IOS-XR | Admin | Enter new password |
Cisco ASA 802 | no username | no passwd, hit enter |
Cisco ASA 8.4.2, 9.1.5 | no username | no passwd, hit enter |
Cisco ASAv | no username | no passwd, hit enter |
Cisco IPS | cisco | ciscoips123 |
Cisco WSA | admin | ironport |
Cisco ESA | admin | ironport |
Cisco WAAS | admin | default |
Cisco XR9K | Cisco | Cisco |
Cisco NX9K | admin | admin |